AWS Organizations (launched in 2017) is a key governance & management service if you are using AWS as a cloud service provider for large or medium scale organization. Key benefits of AWS Organizations are consolidated billing, automated account creation, centralized management of service control policies (SCP), and governance over AWS accounts managed within the organization. As there is no additional charge for using AWS Organizations, it is encouraged to reap the benefits of this service.
These are key learning based on practical knowledge of using AWS Organizations and essential to ensure that the right governance is in place.
1. Plan Early and Get Consensus on Account Structure
It is recommended to use it in the early stage of AWS setup but if you have already setup AWS account structure, you will need to refactor as per the new account structure. AWS also offers another service, AWS Control Tower, which can be used to setup AWS organizations during Landing Zone setup. Note that currently, AWS Control Tower does not support the nested structure.
As per AWS recommendations, there are 3 multi-account strategies but it is largely dependent on your organization structure. Hence, the recommendation is to choose one of the defined account structure models or use a hybrid-account strategy based on your governance preferences.
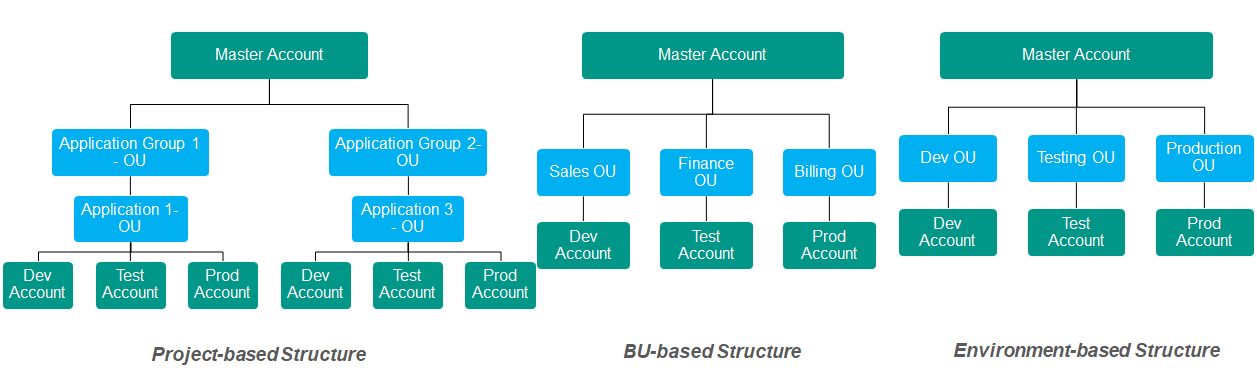
A hyrbid-model with combination of BU-based structure and Project-based structure:
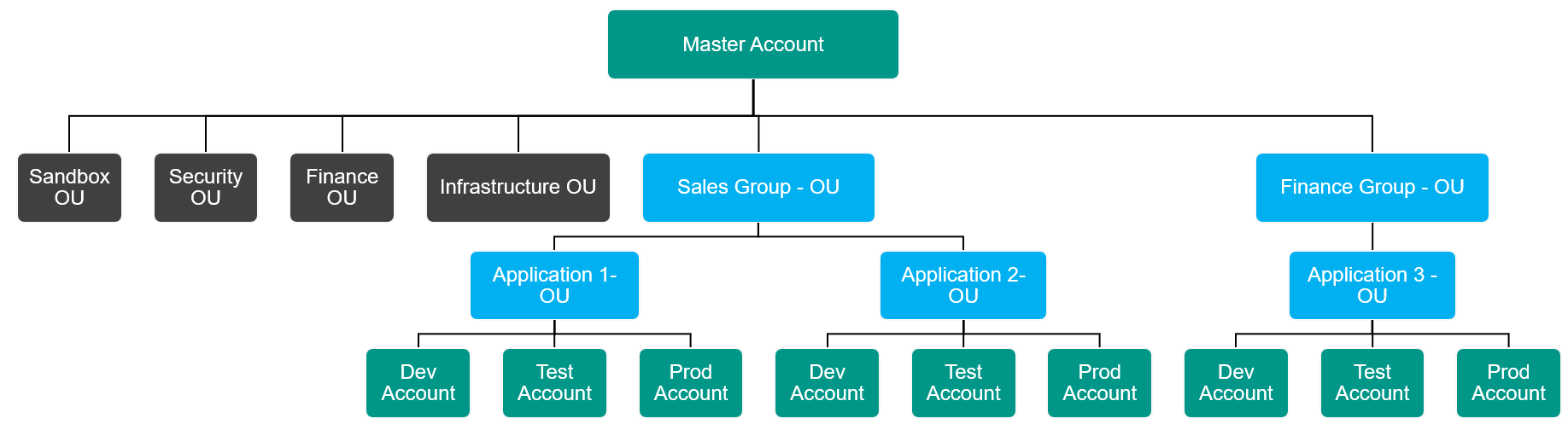

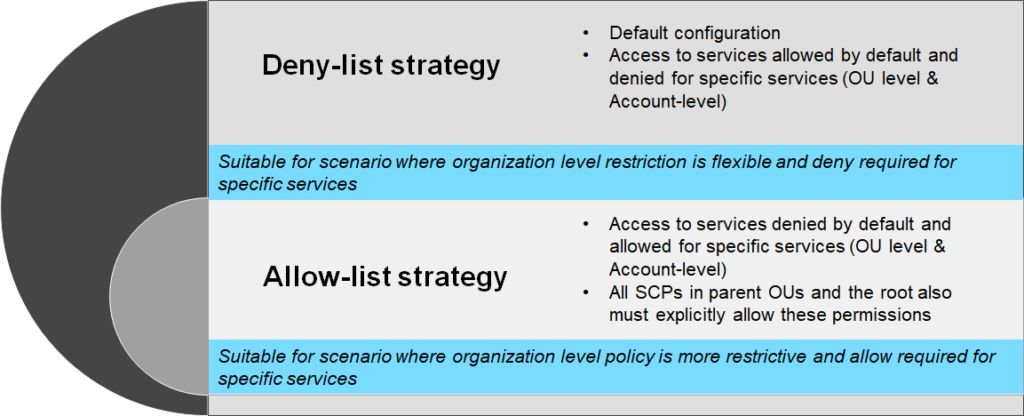
2. Decide on SCP Policy Strategy
SCP (Service Control Policy) is the mechanism to manage permission at the organization and OU level. SCP does not determine the effective permission and only defines the maximum permission an AWS account can have. You can choose between Deny-list strategy or Allow-list strategy based on your governance preference.
Example of Deny-list strategy policy:
{
"Version":"2012-10-17",
"Statement":[
{
"Sid":"AllowsAllActions",
"Effect":"Allow",
"Action":"*",
"Resource":"*"
},
{
"Sid":"DenyRedshift",
"Effect":"Deny",
"Action":"redshift:*",
"Resource":"*"
}
]
}Example of Allow-list strategy policy:
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": [
"ec2:*"
],
"Resource": "*"
}
]
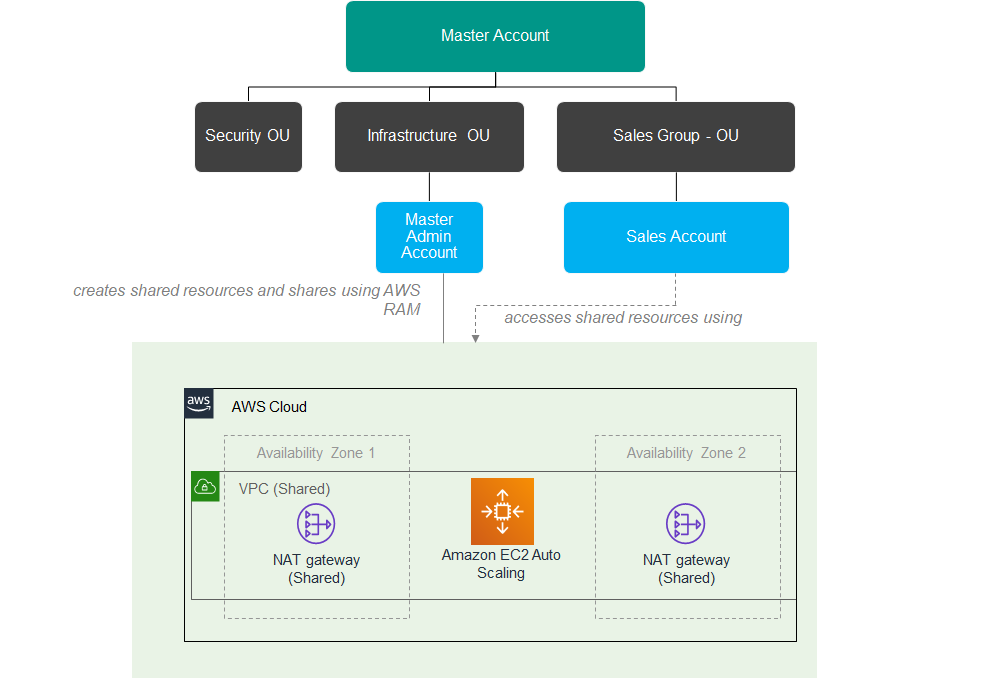
}3. Put Shared Resources in Respective Organization Unit (OU)
In a multi-account setup, it is important to strategize which AWS resources to be shared (e.g. VPC, Subnets, NAT Gateway, etc.) particularly to ensure the right balance between resource control and cost-effectiveness.
For example, if every account has its dedicated VPC and you have connected a particular VPC to your corporate network using AWS Direct Connect, then you need to establish a VPC Peering for each VPC. This will increase the overall cost of maintaining AWS resources.
Below is an example usage scenario, where AWS resources (VPC & NAT Gateway) are shared using AWS Organizations and AWS Resource Access Manager (RAM).
To conclude, AWS Organizations along with supplementary AWS Services help to establish the governance model in a multi-account setup, and utilize the above techniques for better governance. Keep learning continuously and share your feedback and comments!

